 Yesterday I posted an article on how to use PowerShell and the [ADSI] type accelerator to set a local user account. However, if you are running PowerShell 4.0 you have another option: Desired State Configuration (DSC).
Yesterday I posted an article on how to use PowerShell and the [ADSI] type accelerator to set a local user account. However, if you are running PowerShell 4.0 you have another option: Desired State Configuration (DSC).
ManageEngine ADManager Plus - Download Free Trial
Exclusive offer on ADManager Plus for US and UK regions. Claim now!
I'm going to assume you have some basic understanding of how DSC works. If not, head over to the Public OneDrive folder for PowerShell.org and grab a copy of the free DSC ebook.
DSC ships with a provider resource for user accounts.
Because of the account password, the official stance is to use a certificate to handle encrypting the password. You can read about that on the PowerShell team blog. But that's more than I want to deal with right now, plus I trust the security of my local test network so my configurations will store the passwords as plain text in the resulting MOFs. I suppose I should show you the script I came up with.
#requires -version 4.0
#requires -RunasAdministrator
param(
[Parameter(Position=0,Mandatory)]
[ValidatePattern("^CHI")]
[string[]]$Computername
)
Configuration LocalUserAccounts {
Param(
[Parameter(Position=0,Mandatory)]
[ValidatePattern("^CHI")]
[string[]]$Computername,
[Parameter(Position=1,Mandatory)]
[PScredential]$Password
)
Node $Computername {
User LocalAdmin {
UserName="localadmin"
Description="Local administrator account"
Disabled=$False
Ensure="Present"
Password=$Password
}
#add the account to the Administrators group
Group Administrators {
GroupName="Administrators"
DependsOn="[User]LocalAdmin"
MembersToInclude="localadmin"
}
} #node
} #end configuration
#create config data to allow plain text passwords
$ConfigData=@{AllNodes=$Null}
#initialize an array for node information
$nodes=@()
foreach ($computer in $computername) {
#write-host "Adding $computer" -foreground green
#define a hashtable for each computername and add to the nodes array
$nodes+=@{
NodeName = "$computer"
PSDscAllowPlainTextPassword=$true
}
}
#add the nodes to AllNodes
$ConfigData.AllNodes = $nodes
#you will be prompted to enter a credential
Write-Host "Enter the credential for localadmin" -foregroundcolor green
#create the configurations
localuseraccounts $computername -configurationdata $configdata -OutputPath c:\scripts\LocalUserAccounts
This script is intended to define a set of MOFs for computers in my Globomantics domain that all start with "CHI". The script takes an array of computernames. From there it defines the configuration, defines the necessary configuration data to allow plain text passwords and then executes the configuration. The configuration also has a Group resource to add the account to the local Administrators group. Note the DependsOn setting in the group configuration. This ensures that the account will be set up before adding it to the group.
To create the configurations I run my script specifying the computer names.
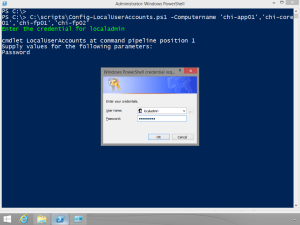
PowerShell will prompt me for the credentials. When finished I am left with a MOF file for each computer under C:\Scripts\LocalUserAccounts, because I specified an output path. When I'm ready, I can push the configuration to the servers:
Start-DSCConfiguration -path c:\scripts\localuseraccounts
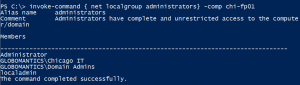
And that's it! I can verify using the NET USER command in a remote session.
DSC promises to change the way IT Pros get their work done, and in a positive way!

I was just wondering what we could leverage DSC to do. This is a great idea. Use DSC to manage those troublesome local settings like local accounts.
Thanks Jeff
Be aware that my example is putting the password in clear text in the MOF. The better way uses certificates and encryption.
I know but the idea is worth it. We can use DSC for other local account issue that can be a headache to maintain or change.
It would be nice if Microsoft extended GP to use some elements of DSC. Managing change is important. It needs to be effortless.