It seems I'm always seeing requests and problems on getting local user accounts using PowerShell. However, even though we are at PowerShell 5.0, Microsoft has never released a set of cmdlets for managing local user accounts. So many of us have resorted to creating our own tools. I now have my latest iteration of a function to get local user account information from remote computers.
ManageEngine ADManager Plus - Download Free Trial
Exclusive offer on ADManager Plus for US and UK regions. Claim now!
The function takes a shortcut of sorts by using the ADSI type accelerator to connect to a remote computer. This is the same technique we used back in the VBScript days. However, this technique isn't conducive to alternate credentials and requires legacy protocols like RPC and DCOM. But that isn't necessarily an issue as I'll show you in a few minutes.
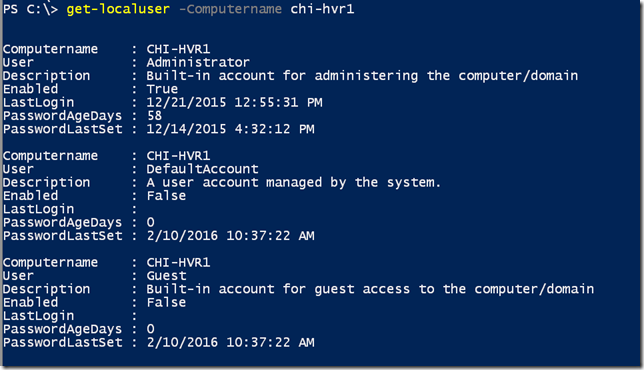
The function connects to the remote computer and then uses some COM object voodoo, to enumerate local account information. By default, the command will list all user accounts.
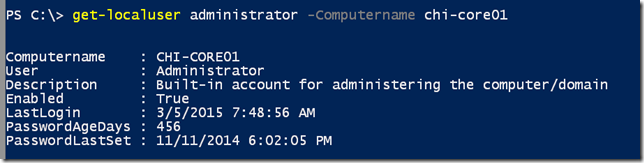
Or you can specify a single user account name.
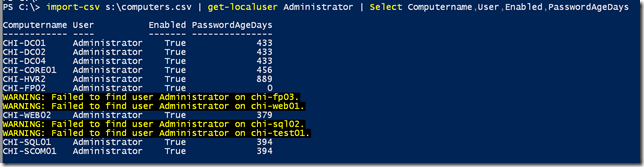
The function accepts pipeline input making it easy to check multiple servers at once.
import-csv s:\computers.csv | get-localuser Administrator | Select Computername,User,Enabled,PasswordAgeDays
On important note: if you query a domain controller you will get domain accounts.
Remember I mentioned this command uses legacy protocols. One alternative is to use PowerShell remoting and Invoke-Command. First, create the necessary PSSessions, using alternate credentials if necessary.
$s = new-pssession -computer chi-core01,chi-web02,chi-fp02
Then get the function's scriptblock.
$sb = ${function:Get-localuser}
Now you can use this with Invoke-Command:
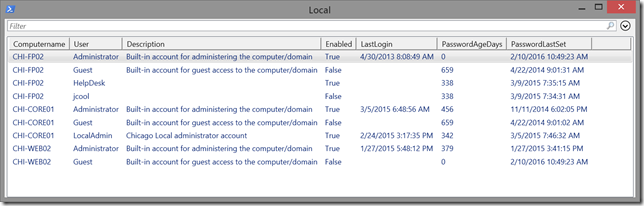
invoke-command -scriptblock $sb -session $s -hidecomputername | select * -exclude RunspaceID | out-gridview -title "Local"
Or query for a specify account:
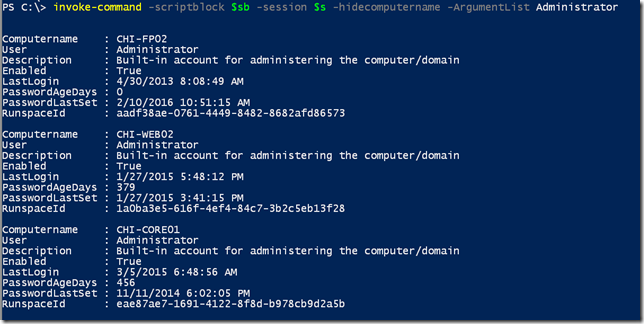
invoke-command -scriptblock $sb -session $s -hidecomputername -ArgumentList Administrator
You can find the complete script, which includes an alias on Github.
I hope you'll let me know what you think and that you find this a useful addition to your PowerShell toolbox. If you run into problems, please post them on the Gist page.

That’s a good addition to my Set-LocalUser function:
https://github.com/megamorf/PowerShell-Stuff/blob/master/LocalUserManagement/Set-LocalUser.ps1